Next named exclusive Trail Blazer in NEW 2024 Radicati DLP Market Quadrant Report
Read the Report
US Federal agencies, large enterprises, or small-medium businesses: Do you need to make sure you adhere to the NIST Cybersecurity Framework and NIST 800-53? Save time and paperwork by utilizing Reveal’s power search.
The National Institute of Standards and Technology (NIST), a part of the U.S. Commerce Department, is responsible for developing and enabling information security standards and guidelines across federal agencies. NIST has published the NIST Framework for Improving Critical Infrastructure Cybersecurity (“Cybersecurity Framework”) and NIST Special Publication 800-53 (“NIST SP 800-53”).
NIST developed the voluntary risk-based Cybersecurity Framework following executive order 13636 issued by former President Obama in 2013. The Cybersecurity Framework is a private sector and government-led effort as a “how-to” guide with global standards, best practices, and approaches, sharing cybersecurity threat information to manage cybersecurity risks to critical infrastructure.
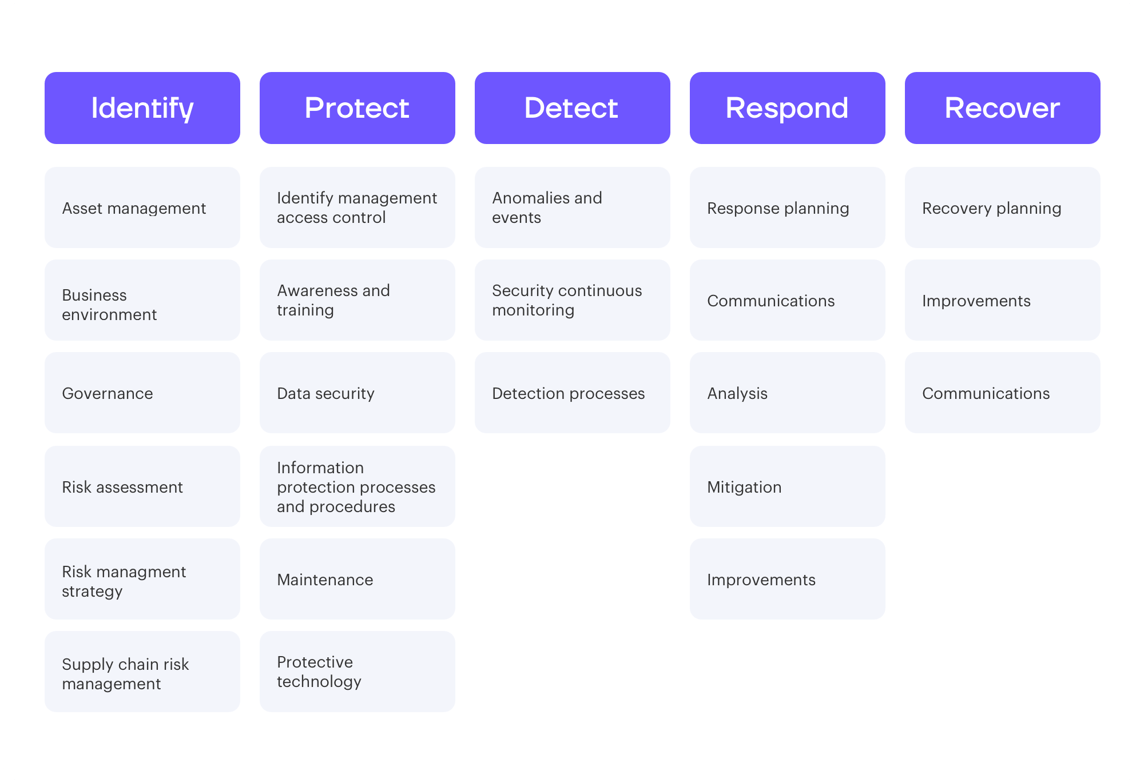
The framework is divided into five different functions: identify, protect, detect, respond, and recover.
Following executive order 13800 issued May 11, 2017, by President Donald J. Trump, all US heads of executive departments and agencies (“agency heads”) are held accountable for managing cybersecurity risk. Within 90 days of the executive order, all agency heads had to produce a risk management report, containing “the risk mitigation and acceptance choices made by each agency head as of the date of this order” and the agency’s action plan to implement the Cybersecurity Framework.
NIST SP 800-53 is also known as the Security and Privacy Controls for Information Systems and Organizations. The NIST SP 800-53 includes a list over 300 security controls to ensure minimum requirements for federal information systems. The document’s security controls support the Cybersecurity Framework, as well as the Risk Management Framework and Systems Engineering Processes.
The security controls in NIST SP 800-53 provide standards and guidelines for federal agencies and organizations, to protect “operations and assets, individuals, other organizations, and the Nation from a diverse set of threats including hostile attacks, national disasters, structural failures, human errors, and privacy risks” (NIST SP 800-53).
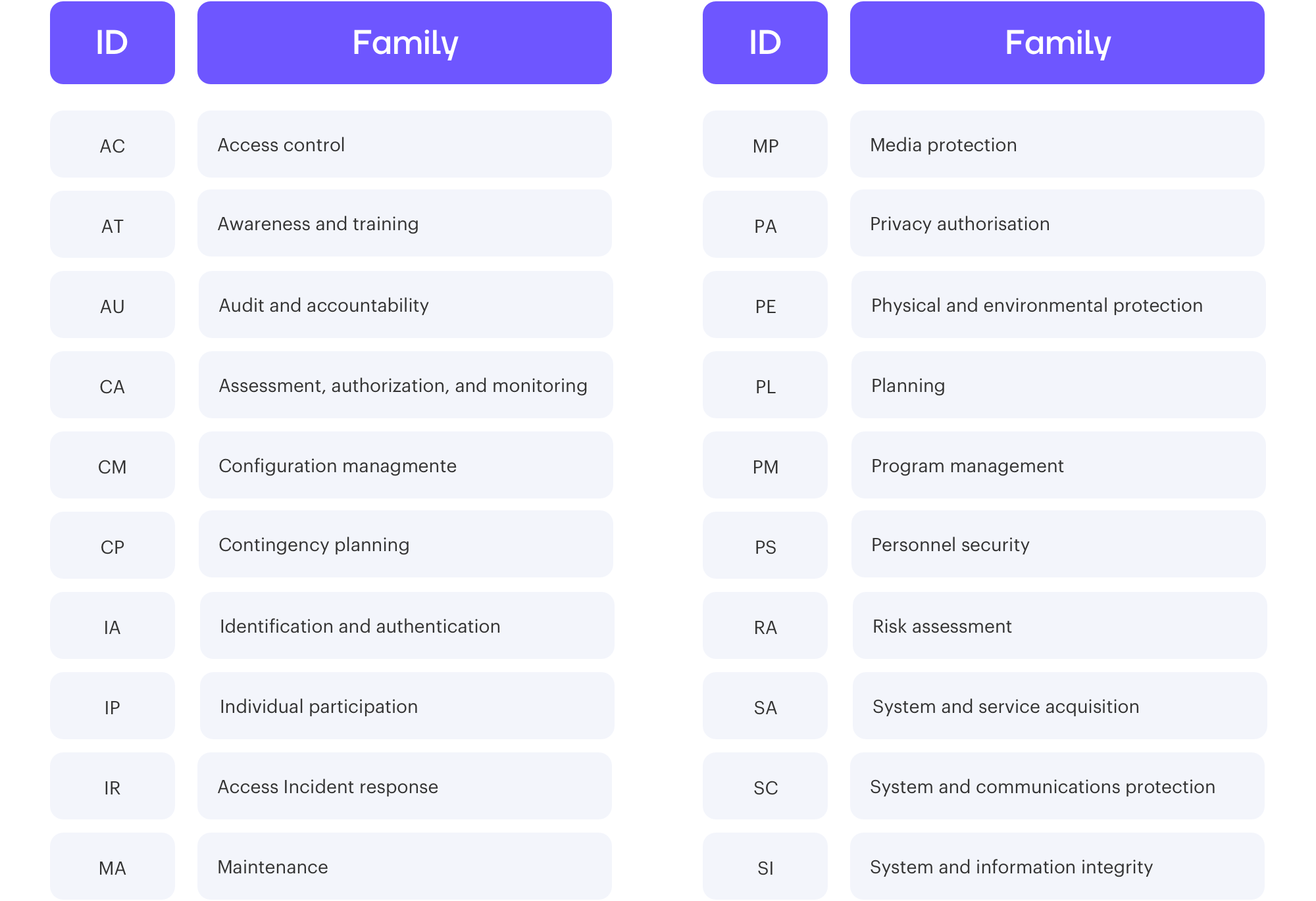
18 control families, categorized in three classes based on impact (low, moderate, and high)
NIST 800-53 is a living document that includes security controls to secure your organization. The major change of revision 5 of NIST 800-53 is addressing all systems, no longer limited to Federal systems, including “a proactive and systemic approach to develop and make available to a broad base of public and private sector organizations, a comprehensive set of safeguarding measures for all types of computing platforms, including general purpose computing systems, cyber-physical systems, cloud and mobile systems, industrial/process control systems, and Internet of Things (IoT) devices” SP 800-53 Rev. 5.
The goal is to protect organizations from attacks, limit the damage when attacks happen, as well as making the systems resilient and survivable when attacks occur.
By mapping the security controls, you can use Reveal’s power search to audit your own organization before going through an external audit. By simply/quickly auditing your own organization, you save time and avoid the pain of time-consuming paperwork.
The power search allows you to quickly access historical context. Search through millions of data records by zooming in from months to minutes of data within seconds.
Check whether you are compliant to the NIST 800.53 controls with a POC using Reveal. By utilizing Reveal’s power search you can easily find out if you are adhering to, for example:
Account management:
Specify authorized users of the system, group, and role membership, and access authorizations (i.e., privileges) and other attributes (as required) for each account
Monitor the use of system accounts
Align account management processes with personnel termination and transfer processes
Account monitoring for atypical usage
Disable accounts for high-risk individuals
Access enforcement:
Revocation of access authorizations
Restrict access to specific information
Attribute-based access control
All US federal agencies must follow NIST Cybersecurity Framework according to executive order 13800, while the private sector and enterprises are recommended to follow it. The Cybersecurity Frameworks is also considered a roadmap for organizations developing their cybersecurity practices, as well as a guide for SMB companies.
The Cybersecurity Framework is highly recommended to all organizations, no matter size, cybersecurity risk, and security team size. The Cybersecurity Framework focuses on affordable ways for you to protect your organization–ways that are working in the global industry today.
Complying with the Cybersecurity Framework and SP 800-53 will help your organization to be compliant with other government regulations–HIPAA, PCI DSS, or GDPR.
As the Cybersecurity Framework is based on global recognized “best standards”, the framework applies to organizations beyond US Federal and the United States.
Any established organization (federal or not) have a number of security products to protect the organization and its asset.
Can you audit yourself to see if you are compliant to government regulations (and other?)?
Do you have an easy, time-efficient way to see which areas you are not covered?
By using Reveal's power search, you can both audit yourself, as well as see which gaps you need to address. Finding your gaps can save you time and paperwork before an external audit. Reveal’s power search is the search engine of cybersecurity, providing easy-to-use search, where you visually see the results, and ability to dig to the core of anything that has happened in your organization.
Reveal extends beyond the power search. We can help you become compliant with modules such as User Behavior Analysis (UBA), alerts, Multi-Factor Authentication (MFA), and actions. Read our extensive guide to what is Nist 800-53.

Blog

Blog

Blog

Blog

Resources

Resources

Resources

Resources